What is GDAP?
Responding to the growing security and compliance concerns Microsoft is reinforcing customer access control capabilities by introducing the Granular Delegated Admin Privileges (GDAP).GDAP refers to all Microsoft Direct Bill Partners, Indirect Providers, and Indirect Resellers in Cloud Solution Provider (CSP) Program, including all Microsoft 365 products, Microsoft Dynamics 365, Microsoft Power Platform, and Microsoft Azure.
GDAP is a natural transformation of Delegated Admin Privileges (DAP) which allows partners to service customers, at the same time reducing security risks by enabling custom roles and access time limit constraints - as a result, the GDAP process will override the current DAP (DAP model has indiscriminate access, which cannot be controlled on a more granular level).
The downside of the prevailing DAP security feature is that many customers can’t feel safe choosing Microsoft services because the partner gets global admin access to the customer data and workloads. So, in case a partner account is compromised, the data of customers can also be compromised. GDAP eliminates this downside as customers can now choose to limit access to its data and workloads by giving custom permissions instead of allowing global admin access.
DAP vs. GDAP
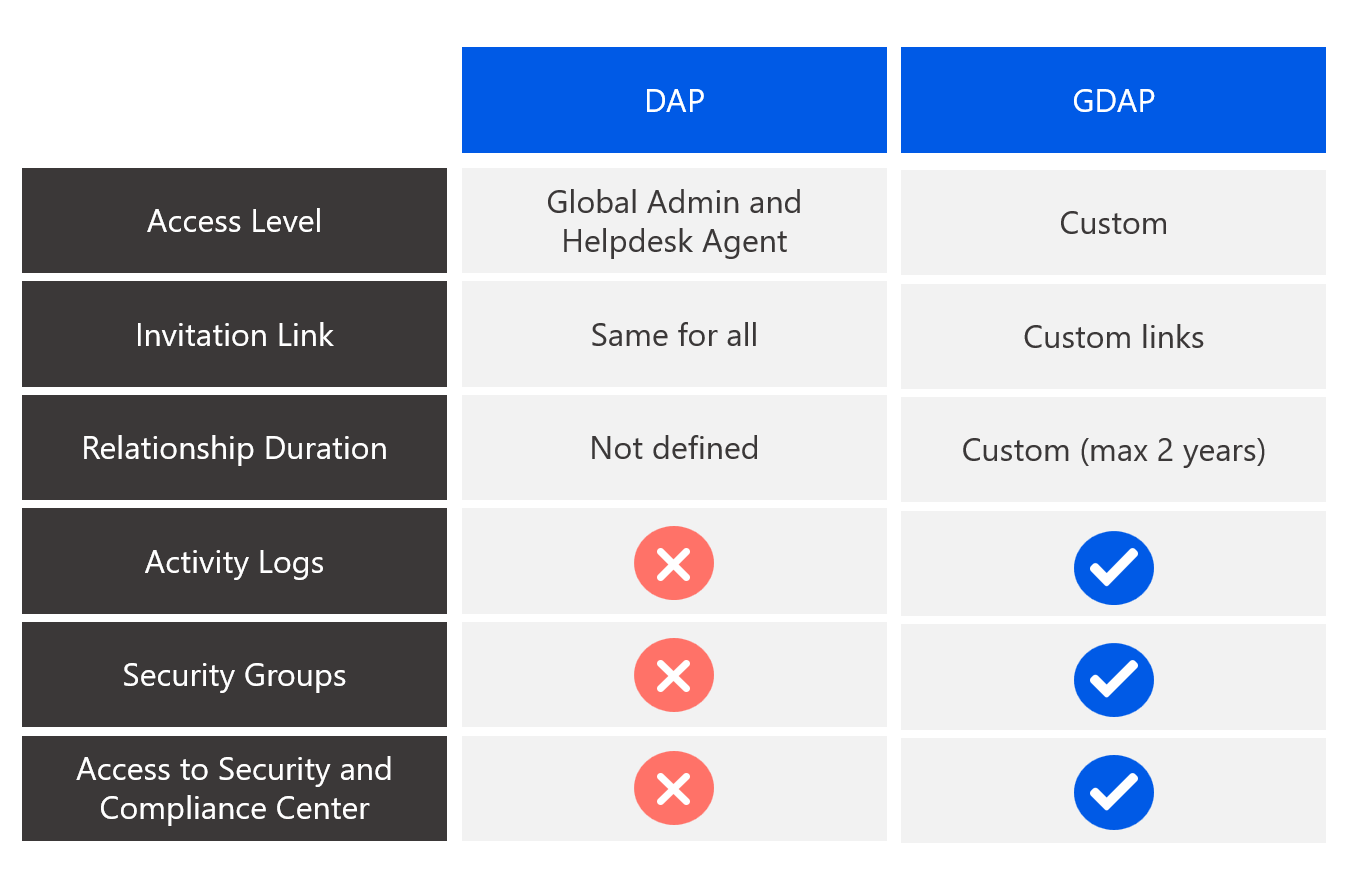
Customers will no longer be required to grant admin permissions to partners, instead, acting partners will be able to tailor relationship access rights towards their customers based on their customer security compliance requirements in terms of access controls (e.g. Least privilege principle, which would only require a partner to operate as CSP support and Teams or Dynamics Service Administrator exclusively).
With GDAP, partners also no longer have access to all customer tenants across Azure subscriptions through Admin agents by default. Instead, partners managing Azure are part of a separate security group, which is a member of the Admin agent group. This group grants owner role-based access control (RBAC) access on all Azure subscriptions for that customer. These changes will allow partners to utilize the minimum access rights needed that correspond with the scope of support that customers expect to receive.
In addition, GDAP comes with extended visibility and granular activity logs that illustrate when GDAP permissions are being used along with the lifecycle of that relationship.
New GDAP milestone dates
The new timelines of Microsoft are providing partners with more time to make the transition from delegated admin privileges (DAP) to granular delegated admin privileges (GDAP).
Transition active and inactive DAPs: Starting May 22, 2023
- Microsoft will begin transitioning active and inactive DAP relationships to GDAP with limited Azure Active Directory (AD) roles. We will provide clarity on the roles by March 15, 2023.
- For relationships that have been transitioned from DAP to GDAP, we will proceed to remove the corresponding DAP relationships 30 days later.
- Microsoft will pause the transition for the month of June to support the fiscal year closure.
The dates for the following milestones will be communicated on March 15, 2023:
-
- Stop new DAPs—DAP is currently granted when a new customer tenant is created. Microsoft will no longer grant DAP for new customer creation.
- Grant GDAP default roles for new customers—GDAP with certain default roles will be granted when a new customer tenant is created.
- Retire the bulk migration tool—The bulk migration tool will be retired.
- Bulk migration tool: New DAP removal feature
- Starting February 15, 2023, the tool will have a new feature that allows partners to remove DAP relationships in bulk.
- The tool will also be able to carry out bulk editing, deletion of access assignments, and deletion of GDAP relationships. For more details, go to GDAP bulk migration tool.
- The GDAP v1 APIs are now available. We recommend moving from beta to v1.0 as soon as possible.
- It was required that every privileged access group (formerly called PIM for Groups feature) had to be a role-assignable group. This restriction has now been removed. It’s now possible to enable more than 500 groups per tenant in PIM; however only up to 500 groups can be role assignable. For more information, refer to Privileged Identity Management (PIM) for Groups (preview) - Azure Active Directory.
- You should add a security contact now to receive Azure fraud notification emails. These emails are currently being sent to the admin agents, but if an admit agent is just-in-time (JIT) enabled and the JIT expires, the email won’t be delivered. Hence, having a security contact will help detect and protect Azure fraud events. Learn more about handling Azure fraud notifications. We recommend investigating and updating the fraud event status.
Important! If GDAP is not enabled on customer tenants, partners will cease to receive Partner Earned Credits and Incentives and will not be able to provide CSP Support.
To avoid disruption to your business, we recommend that you do not delay and take action now to transition to GDAP for the level of access that you require to manage your customers. The limited GDAP roles (Directory reader, Global reader, User administrator, License administrator, Service support administrator, and Helpdesk administrator) granted by Microsoft during the transition will only allow you to perform least-privilege activities. All other access permissions (for example, access to Exchange workloads) will be lost, and in order to perform all other activities, additional GDAP roles will be required to be granted by the customer.
Call to action
- Audit Existing DAP Connections (from here). In Microsoft Partner Center, you have access to a reporting tool that identifies and displays all active connections with delegated administrative privileges and helps you discover inactive DAP connections.
- Remove inactive DAP Connections (from here). Identify inactive DAP connections and delete them as soon as possible.
- Start Planning for Your DAP-to-GDAP Transition. Identify what activities your users perform in the customer portal to determine which GDAP roles will be most applicable.
- Transition to GDAP using the GDAP Bulk Migration tool or AppXite GDAP Migration Solution for AppXite platform users.
- Disable DAP. Once your customer has granted you GDAP and confirmed that you can perform all necessary administrative activities on behalf of your customer, you must disable your existing DAP connection.
- Add a security contact in Partner Center.
GDAP Migration Solution for AppXite platform users
We are pleased to announce that AppXite released a custom GDAP migration solution that will significantly speed up the DAP-to-GDAP migration and simplify the GDAP relationship management.
AppXite Partner Management Solution can be used (free of charge) by any Direct and Indirect Microsoft partners using the AppXite Platform. Download it now from Microsoft Store.
Why is AppXite Partner Management Solution convenient for you?
- It is developed to operate seamlessly on your Microsoft automation platform provided by AppXite.
- It is a 100% self-service solution and by following our extensive tutorials, the GDAP migration won’t put any strain on your business.
- It is flexible enough so you can tailor it to fit your own business need e.g. different security groups for different customers.
- It is already available for you, so you don’t need to look for workarounds or design extensive migration plans.
- It is tried and tested by AppXite, and you can reach out to us for additional guidance if you stumble upon a roadblock.
- And you can add it to your tech stack now.
Find out more about the solution's capabilities from our GDAP how-to tutorials:
1. GDAP - Software Client Setup
2. GDAP - User Account Registration & Activation
3. GDAP - CSP Roles / Template Management / Security Group Provisioning
4. GDAP - Customer Transition and Synchronization
.png)
